TGIF, readers.
Listen, just a super quick anecdotal start to this story:
While I certainly don’t recommend falling into the habit of checking social apps literally first thing upon waking, I can’t truthfully say that I didn’t do that very thing this morning…
… anyway, trust me. It’s relevant.
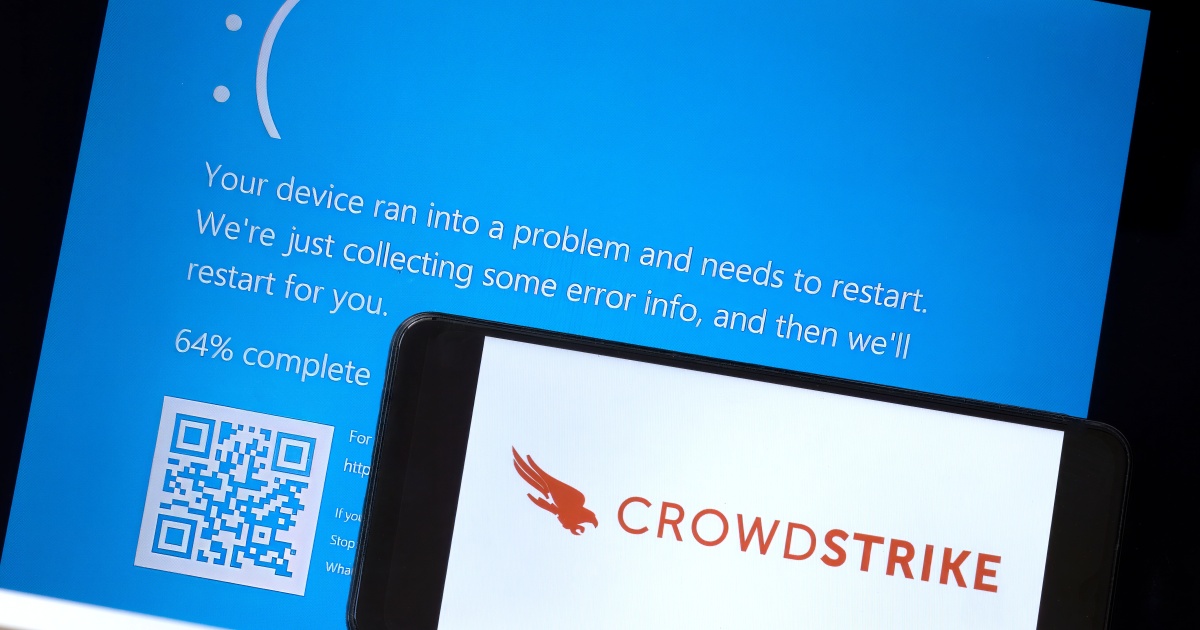
This image from Twitter/X was the first to grace my feed today.
So, what happened? A strange isolated incident at the Sphere in Vegas, perhaps?
Unfortunately, while some users are saying the above image could’ve been edited in order to boost online engagement, it nevertheless puts actually warranted attention on something that is very much real. Sphere regardless, this same Blue Screen of Death (BSOD) has full-on flooded social media in recent hours; individuals have seen it “in airports, banks and other businesses” in what appears to partly stem “from a software update issued by major U.S. cybersecurity firm CrowdStrike,” according to CNN a few hours ago.
A complex problem has arisen.
What’s happened isn’t limited to airports or banks; healthcare institutions, hotels and TV stations (to name a few) all experienced their share of this incredibly widespread outage, which is why Windows displayed BSODs for users worldwide.
Right away, CrowdStrike put out a statement; its CEO George Kurtz explained that the outages were indeed reportedly caused by “a defect found in a single content update for Windows hosts.”
“This is not a security incident or cyberattack,” Kurts continued. “The issue has been identified, isolated and a fix has been deployed. We refer customers to the support portal for the latest updates, and we will continue to provide complete and continuous updates on our website. We further recommend organizations ensure they’re communicating with CrowdStrike representatives through official channels. Our team is fully mobilized to ensure the security and stability of CrowdStrike customers.”
So essentially, a.) we’re talking about a modification to a line of code in a misconfigured update that was pushed, and b.) CrowdStrike is on top of it. The issue is specific to Falcon, a major CrowdStrike software product, and this doesn’t appear to have impacted Mac or Linux operating systems.
Some aren’t yet content, though. Conversations that are kicking up dust, so to speak, seem to be ranging from casually (yet worryingly) “where were you during the global IT meltdown?” to more serious urging for further oversight when it comes to “critical, fundamental weaknesses in proprietary software and the unilateral authority to push updates.”
Still, CrowdStrike further assured users, stating “We understand the gravity of the situation and are deeply sorry for the inconvenience and disruption. We are working with all those impacted to ensure that systems are back up and they can deliver the services that people are counting on. Our customers remain fully protected.”
That’s key – trust. While not a malicious cybersecurity issue (and while customers retain their protections), this still creates due concern. Cybersecurity researcher and consultant Lukasz Olejnik described it succinctly, saying “It reminds us about our dependence on IT and software. When a system has several software systems maintained by various vendors, this is equivalent to placing trust on them. They may be a single point of failure – of paralysis – like here, when various firms experience the impact.”
As of this article’s publication, CrowdStrike has since put out steps to remediate.
Edited by
Greg Tavarez






