Numerous organizations dedicate substantial resources and funds toward disaster recovery (DR) and technology resilience initiatives. These initiatives aim to prepare and protect organizations from potential disasters or disruptions, such as natural disasters, cyberattacks, system failures or other unforeseen events that could negatively impact their operations.
Despite these investments, the organizations lack an understanding of whether these efforts are yielding the anticipated benefits or providing the expected value. In other words, they are unsure if the resources allocated to DR and technology resilience are effectively mitigating risks and enabling them to recover quickly and efficiently in the face of adverse events.
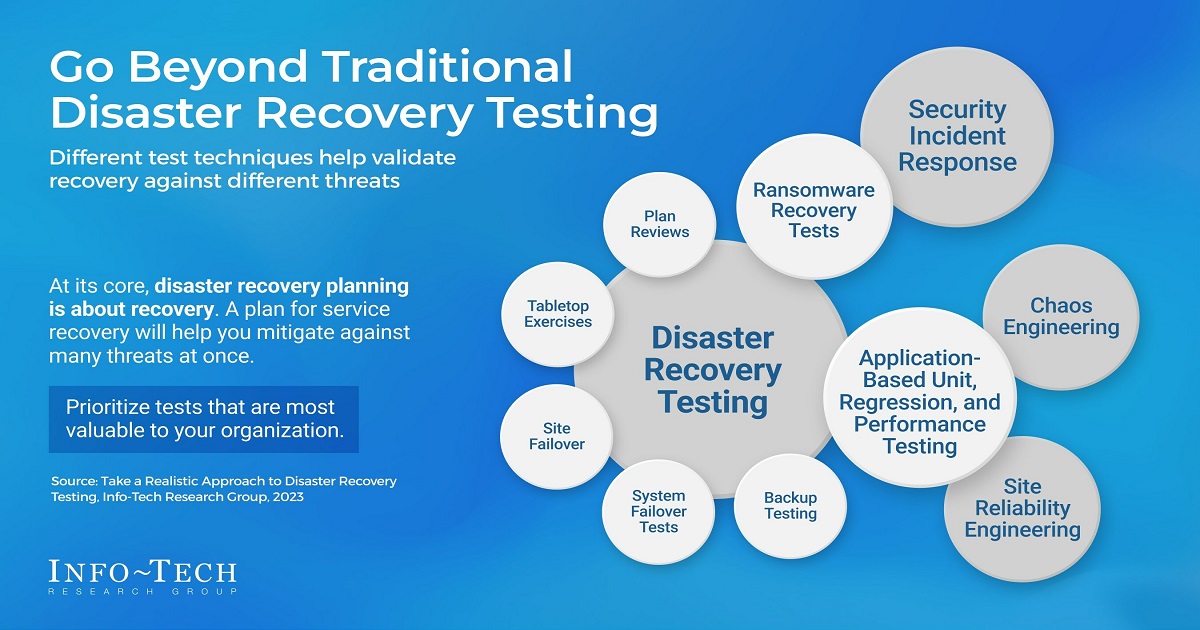
Info-Tech advises, in a new research-backed blueprint, that the best way to determine if existing DR processes meet business requirements and provide service continuity is by regularly testing recovery processes and systems.
Of course, that is easier said than done. So, in the blueprint, Info-Tech highlights seven steps that IT leaders can follow to validate recovery capabilities and enhance service reliability, availability and continuity.
- Formulate a working group: IT leaders should assemble a team consisting of representatives from IT operations, cybersecurity, business continuity and key stakeholders from different departments (such as finance, human resources and operations). The purpose is to have individuals who provide valuable insights and inputs for testing in the research process. Remember, it is possible for one person to fulfill multiple roles, and some roles can be shared among multiple individuals.
- Establish the purpose of testing: Leaders must determine the significance of recovery testing for their organization. Here, the IT leaders explain to the working group that conducting recovery testing ensures that critical systems and data can be restored and business operations can resume smoothly in the event of a disaster. They emphasize the importance of testing in safeguarding the organization's reputation, minimizing financial losses and maintaining customer trust.
- Conduct a tabletop exercise: The working group then gather around a table and uses cue cards to simulate a hypothetical scenario, such as a cybersecurity breach or a natural disaster. They should discuss and collaborate on the steps they would take to respond, recover and restore operations. This exercise can help identify potential gaps or challenges in the existing plan.
- Generate and prioritize test ideas: During this phase, the working group should collaborate to generate innovative testing ideas that might otherwise be overlooked. For example, the working group brainstorms various testing ideas, such as simulating a power outage, testing data recovery from backups or conducting a mock phishing attack to assess employee awareness. They prioritize these ideas based on the potential impact on critical systems, the feasibility of execution and the resources required.
- Develop a test plan: A comprehensive test plan contributes to the smooth execution of tests and helps identify any issues with the underlying disaster recovery plan. The working group can utilize the Disaster Recovery Test Plan Template provided by Info-Tech to create a detailed test plan. They outline the objectives, specific test scenarios, roles and responsibilities, timelines and necessary resources for each test. The plan includes details such as which systems will be tested, the testing methodology and success criteria.
- Conduct an after-action review: Following the test, the working group meets to discuss the outcomes and lessons learned. They review the test plan, assess the effectiveness of the strategies employed and identify any issues or improvements required. They document these findings alongside the test plan for future reference and continuous improvement.
- Create a test program summary: The IT leaders compile a comprehensive summary document that captures the key takeaways, testing goals achieved, significant findings, milestones and recommendations. The summary also includes an overview of the testing cycle, participant roles, and next steps for enhancing the organization's disaster recovery and resilience capabilities. This document serves as a reference for future testing initiatives and aligns with the organization's overall strategic objectives.
"More than just validation, regular disaster recovery testing helps IT deliver service continuity by finding and addressing gaps in existing processes and training staff on recovery procedures" said Andrew Sharp, Research Director in the Infrastructure & Operations practice at Info-Tech. “IT leaders should focus on identifying gaps and risks so they can be addressed before a real disaster hits."
Info-Tech's research insights show that more complex, risky or costly tests deliver significant value but that high-value, low-effort options are often the best place to start. Testing should get easier over time, but if organizations are routinely and easily passing every test, it is a good indicator that IT leaders and the organization are ready to run more challenging tests.
Edited by
Alex Passett






