The cyber insurance industry is in the midst of a seismic shift, mirroring the escalating sophistication of cyber threats. AI-powered attacks have become more prevalent and insidious. In response, insurers are tightening the reins and demanding stringent security measures from potential clients.
This hardening of the market is forcing business to move through a more difficult path; namely, between boosting their defenses to meet heightened underwriting standards, and the continuous pressure to control costs.
Gone are the days of lax security measures and broad coverage. Insurers are now scrutinizing applicants with an eagle eye, demanding MFA, penetration testing and incident response plans. These heightened expectations (while necessary to mitigate risk) have placed burden on businesses, particularly smaller enterprises with limited resources because the cost of implementing these enhanced security measures can be substantial.
The pressure will only continue to mount on businesses to adapt or face the consequences, unfortunately. Those who fail to demonstrate a commitment to better cybersecurity practices may find themselves increasingly isolated in the insurance market. This could lead to higher premiums, limited coverage options or even an inability to secure coverage altogether.
But don’t fret, readers. Info-Tech Research Group's newly published blueprint, Launch Cyber Insurance Support Services, provides technology service providers, or TSPs, “with a strategic framework to help their clients meet rising requirements and navigate the complexities of the cyber insurance lifecycle.”
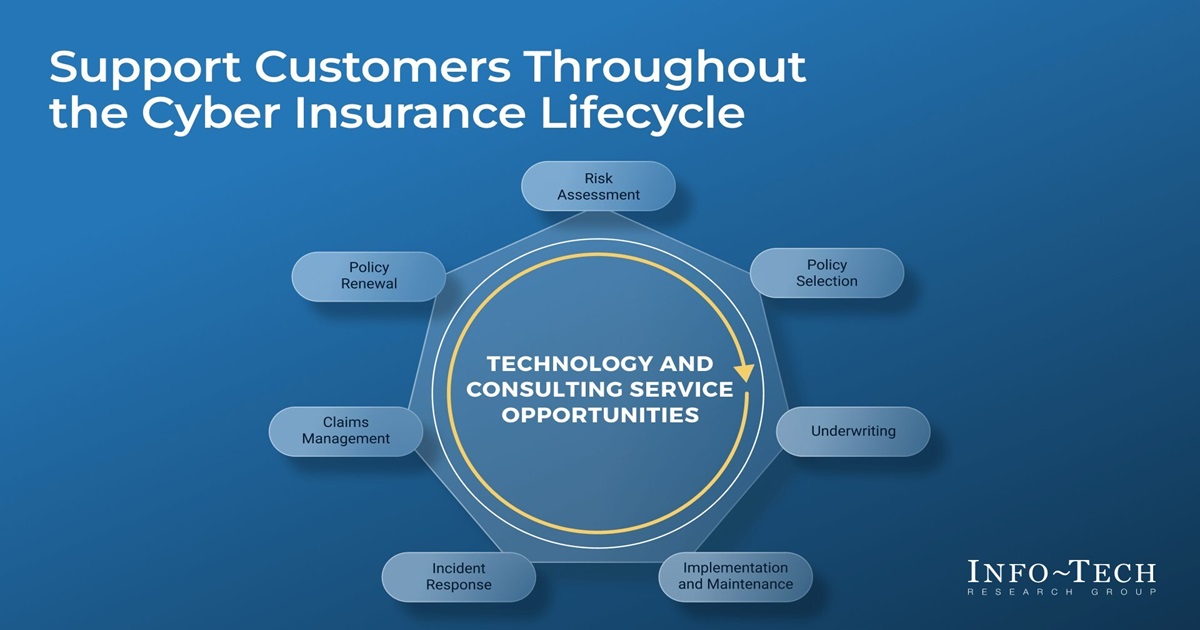
TSPs can enhance operational efficiency and support crucial insurance processes by collaborating effectively with both insurers and their clients. Info-Tech's resource identifies seven key stages within the cyber insurance lifecycle and outlines how TSPs "can contribute meaningfully at each step”
- Risk Assessment: Conduct in-depth cyber risk assessments (including vulnerability scans and threat modeling) to quantify potential losses and identify critical vulnerabilities. Ensure these assessments align with evolving industry standards and specific insurer requirements to accurately reflect the organization's risk profile.
- Policy Selection: Translate the findings of the risk assessment into clear financial terms, such as potential loss estimates and expected recovery costs. Based on this analysis, recommend a range of insurance policies that effectively transfer the identified risks while considering factors like coverage limits, deductibles and exclusions.
- Underwriting: Prepare comprehensive documentation (including detailed security reports, penetration test results and incident response plans) to support the underwriting process. Actively participate in on-site audits, demonstrating the organization's commitment to strong cybersecurity practices and advocating for favorable underwriting considerations based on the organization's risk profile and mitigation efforts.
- Implementation and Maintenance: Continuously monitor and audit cybersecurity controls to ensure ongoing compliance with industry standards and policy requirements. Regularly conduct penetration testing and vulnerability assessments to proactively identify and address emerging threats. Maintain and update security controls based on the latest threat intelligence and best practices.
- Incident Response: Coordinate effectively with insurers during security incidents, providing regular updates on the situation and collaborating to minimize disruption and maximize recovery efforts. Avoid duplication of effort between internal and insurer-led response activities. Ensure all entitled services are utilized effectively to expedite incident resolution and minimize potential losses.
- Claims Management: Prepare detailed claims documentation, including incident reports, forensic evidence and financial impact assessments. Collaborate with insurers to resolve disputes effectively by leveraging technical expertise and providing clear, concise evidence to support the claim. Ensure all claims are processed promptly and in accordance with the terms of the insurance policy.
- Policy Renewal: Regularly assess the effectiveness of modernized cybersecurity practices and their impact on the organization's risk profile. Review insurance usage and identify areas for improvement, such as optimizing coverage limits or exploring alternative coverage options. Renew insurance policies based on current risk assessments, emerging threats and the organization's evolving cybersecurity needs.
“Today, the cyber insurance industry stands at an inflection point, recognizing that previous approaches to security were ineffective and unsustainable,” said Justin St-Maurice, Principal Research Director at Info-Tech Research Group. “Insurers now demand robust due diligence and comprehensive security controls, meaning only organizations with mature security postures will qualify for coverage. As the bar for insurance eligibility continues to rise, customers around the world are scrambling to meet these new requirements.”
The blueprint was created to equip TSPs with practical strategies to position themselves as indispensable partners throughout the cyber insurance lifecycle. Offering tailored advisory and cybersecurity services that meet the needs of policyholders and insurers is a solid way for TSPs to bridge service gaps while optimizing processes such as risk assessment, claims management and policy renewal.
Edited by
Alex Passett






